
You can’t be a professional in an unprofessional industry
Calls to professionalise cybersecurity in Australia often miss the deeper issue: you can't have professional people in a system that isn't professional. This post argues that unless cybersecurity standards are backed by legislation—and enforced independently of employers—they’re just marketing fluff. Real professions have legal backing, independent standards, and consequences for misconduct. Without this, cybersecurity roles remain beholden to commercial interests, powerless to enforce best practices, and vulnerable to retaliation for speaking up. Until we address the structural and economic incentives, cybersecurity professionalism will remain a title, not a guarantee.
Recently, I saw a post by Tony Vizza about the need for professional standards / regulation within Cybersecurity. My replies were critical of the idea, and he probably got the impression I didn't think Cybersecurity required regulation or that it wasn't important.
Which isn't actually the case. I think we can and should do a lot to dramatically improve cybersecurity across all Australian businesses, organisations, and government bodies. The frequent news of breaches provides a clear indicator of how shit things are.
The issue isn't about people though, it's about the function of cybersecurity and the economic/regulatory landscape it operates in.
You can't have Professional people in an industry that isn't Professional.
Let's ignore for the moment the pros and cons of establishing Cybersecurity as a “Profession”. Assume it's a given, and something very similar to the Australian Computer Society standards for Ethics/Practice is put in place. First up, who are these cybersecurity people? When most people think of cybersecurity, they imagine technical people working away behind keyboards to secure technology. This is true to an extent, but there are also many people who came from other disciplines. There is overlap with other functions such as compliance / governance, and you can be in cybersecurity with relatively little technical skills. There are an awful lot of cybersecurity professionals that have never tried to attack or defend a server. They know the importance of secure password policies, but don't know how to reset their password in Active Directory. Who are they working for?
Anyone and everyone, from government departments, companies, non-profits, and consultancies. Most of these roles exist in corporations as an internal function or in a consultancy, as few businesses are big enough to need or afford a full-time function.
So what the problem with creating a “Profession”?
To be a held to any standard when you fill a function, you have to establish the following:
- Your client/employer must also fall under that standard
- Or, at a minimum, can't force you to break the standard
- These constraints need to be enforced by legislation
Without that, all you have is a voluntary framework that some people have decided to follow. If you want to establish something like the ACS, set arbitrary rules and say all members must follow them, knock yourself out. Everyone needs a hobby.
But these types of frameworks don't have any teeth in the real world. They won't improve cybersecurity within Australian entities, and it will just be something for the CV. These sorts of standards are just marketing. You can tell it's just marketing because there's no list of people who have had their membership revoked.
Real professions, share their blacklist so that people know whom to avoid when hiring. ie
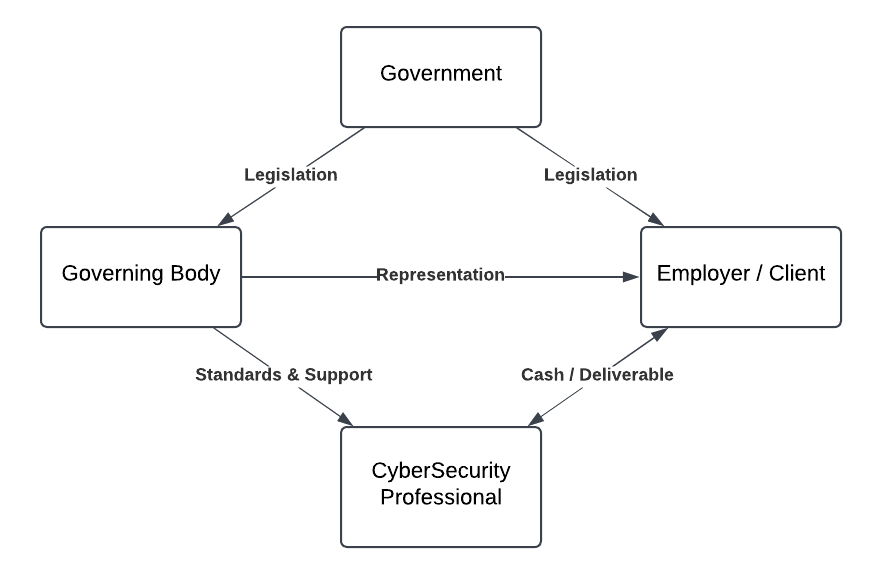
If you want cybersecurity professionals to be bound by a rule, they require legislation that obligates them to do so, while also protecting them in its execution. All the professional standards, have to come from the governing body and supporting law, NOT the employer/customer. The client / employer must have nothing to do with establishing standards.
Think about a doctor. You can have confidence a doctor will keep your itchy rash confidential. However, if it turns out you've got a new STI never seen before by science, they will report your case to relevant people.
You can't stop that report from going in, no matter how much you'd rather it didn't. Nor can the med centre the doctor works at. You can't sue the doctor for breach of contract or defamation etc.
To make professionalisation work, you have to establish a governing body that the members must place before the client when it comes to standards. You are hired by someone true, but you are always loyal to the governing body and standards.
Importantly, the client/employer knows that there is little chance of members abandoning those standards and even less chance of compelling them to do so.
Presently, there is no legislation that defines what “Professional” cybersecurity activity/behaviour even looks like. What cybersecurity legislation exists, is typically broad and consists of recommendations or best-practices.
Which is very deliberate because;
- Corporations have absolutely no interest in binding themselves to a series of legally enforceable cybersecurity obligations that are outside their control. It's bad for business.
- Governments have no interest in pissing off business lobby groups or having companies go broke via penalties. It's bad for your election chances.
Ethics
I'm going to skip most of the ethics conversation. Not because I don't think it's important, or interesting, but because it's subjective. Your idea of ethical, is not my ethical. To give a simple example;
Personally, I would never work for, or have a client that provides gambling services. Sure, it's legal and they have a lot of cash. But I'm not an amoral asshole, hellbent on making money from human tragedy and suffering. That's just me.
The ACS Code of Professional Conduct states that ACS members should:
“protect and promote the health and safety of those affected by your work;” 1.2.2.b
Yet, there are ACS members working in the gambling industry. Go figure.
The employer and cybersecurity authority
Employers have zero interest in cybersecurity staff aligning with a legally binding Professional Standard. It is most definitely is not in their commercial interests. Any real increase in IT security has a very material impact on budgets and timelines.
Companies implement IT security based on three things:
- What they are compelled to do under law
- Within those legal obligations, act on cost vs possible penalties
- Self Preservation, based on how hard stakeholders push, and whether decision makers give a fuck
A cybersecurity professional has zero authority to make anything happen, unless given it by the client/employer. They exist to identify, report and remediate as directed. Nothing more. The CISO can't override a CEO.
Why this Profession, is just a profession
Let's look at a real-world challenge.
- You are auditing systems and notice that the production internet facing servers haven't been patched in over 3 years. They are exposed to multiple CVE's that are actively being exploited in the wild. If they are breached, tens of thousands of customer PII records will be exposed. But no sign of a breach so far!
- You notify leadership, who says that it's a known thing, but there is no time or budget allocated, so they are not going to patch them. It's SOP at the business to kick patching down the road.
What's a Cybersecurity Professional to do?
In the ACS code, it states that:
- “In your work, you should safeguard the interests of your immediate stakeholders, provided that these interests do not conflict with the duty and loyalty you owe to the public“ (The Primacy of the Public Interest 1.2.1)
- “advise your stakeholders as soon as possible of any conflicts of interest or conscientious objections that you have;“ (The Primacy of the Public Interest 1.2.1.b)
- “Not remain silent when you detect unprofessional conduct.” (Honesty 2.1.a)
It would clearly be unethical to simply ignore this situation. Before you throw yourself on your sword though, let's check the companies position. Surely, the Australian Privacy Act 1988 has your back right?
Yeah, not so much. The Privacy act has 448 pages, but you won't find “you must patch servers” in the legislation. You will find this item in “APP 11 Security of personal information”:
“An APP entity that holds personal information must take reasonable steps to protect the information from misuse, interference and loss, as well as unauthorised access, modification or disclosure “
Unfortunately, this isn't as helpful as you might think. The key word here is “reasonable”.
Reasonable is very much up for debate and takes an awful lot of things into consideration. The cybersecurity professional, public, company, and courts are all going to have very different ideas of what “reasonable” means. In this case, the company will say that patching the servers is very unreasonable for a long list of reasons. One being “Fuck you, I hired you to fix my shit not give me grief about patching servers.”
In the end, the big problem is commercial risk vs reward. The company has been running the gauntlet so far, and cant see a reason to change. They have put the servers in the risk register, and it's flagged for discussion in next quarter's budget. In the interim, they are willing to take the risk of a hack.
Even if they get hacked, the likelihood of the OAIC taking them to court is very low. The chance of a fine is astronomically small.
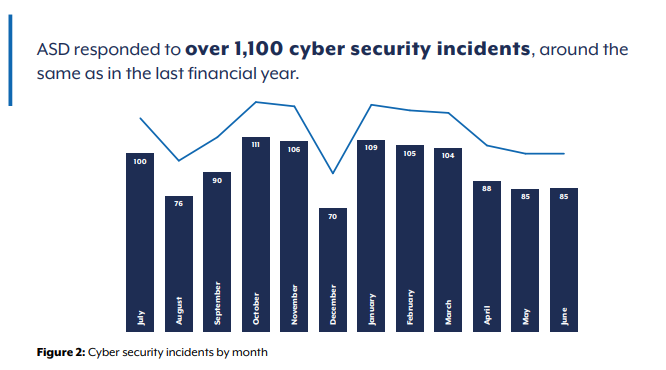
The ASD responded to some 1100 incidents in 2024, so breaches are pretty common.
Surely, the OAIC found some of these companies had breached the Privacy Act and punished them? Lets check:
Enforceable Undertakings: 2
- Inspiring Vacations: 100k records exposed via S3 bucket, but they promised to do better. No fine.
- Meta: The Cambridge Analytica mess. Meta promised not to do it again and paid $50M in penalty. Which sounds like a lot, until you realise it's less than 1% of Australian annual revenue, and only slightly more than Zuck spends on shoes.
Court Cases: 10
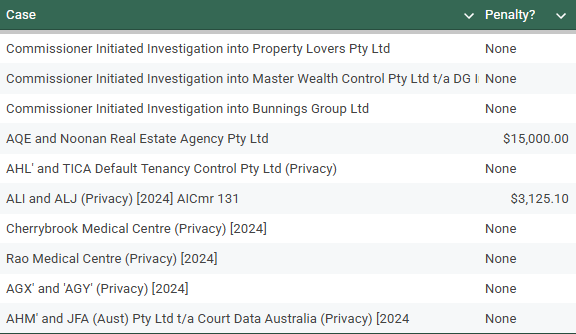
Of the ten court cases I could find in relation to the Australian Privacy Act, all got found guilty of a breach. Only 2 got fines (the ten cents is amusing).
The message is clear, companies really don't give have to care about the OAIC and the Australian Privacy Act. My pet Chihuahua x poodle cross has more bite.

So where does that leave our ethical Cybersecurity Professional?
- The governing body standards are clear, working on this project would be unethical.
- The employer has listened to, and dismissed the request to patch
- The employer isn't going to resolve the issue and has no legal obligation to patch.
- They have no fear of the OAIC, should they be breached.
You could leak the information. If you're very lucky, there is a whistleblower clause in your contract to avoid the NDA you undoubtably signed. Either way, you can kiss your career goodbye in that company.
If word gets out you leak, you can forget finding another gig in cyber. You sure as fuck won't be working for a cybersecurity consultancy. An ex hacker/criminal is one thing, but nobody will touch a corporate snitch.
You can quit, but the rent won't pay itself. Have fun explaining to your family why the bills are overdue because you prioritised server patching.
Now I'm just some uneducated, uncertified, unprofessional tech guy; but how's this professionalism thing meant to work again?
PS
One last thing, if you're an advocate for cybersecurity and professionalism, I think it's a good idea to practice what you preach. There are 11 members of the ACS Technical Advisory Board, 4 make up the cybersecurity board. Each with LinkedIn profiles pointing to their respective websites.
That includes:
- Link pointing to an expired domain with dropcatch. Domain hijack waiting to happen.
- A self-hosted WordPress server that is 6 minor releases behind, that runs on a VPS that is also an SMTP, POP3 and DNS server
- A self-hosted WordPress site on VPS that is also an FTP, DNS, SMTP, POP3 server
- A self-hosted IIS server on VPS that is also an FTP server
- A self-hosted WordPress that is also an SMTP, POP3, DNS and FTP server
- Website on VPS that is also an FTP, SMTP, DNS, and DB server (with DB connection open to the internet)
- Self hosted WordPress on VPS that is also an FTP, DNS, SMTP server
- Site down, expired domain