
You want fries with that password
Published on July 16, 2025 - Updated on August 10, 2025 - Author: David ChealMcDonald's hiring chatbot didn't implode because of AI; it's a case study in systemic security failure—spanning identity, architecture, and DevOps—rubber-stamped by compliance.
I've got some time while my AWS infra deploys, so let's talk about McDonald's and Paradox.
There was a Cybersecurity incident recently impacting the McDonald's hiring chatbot. WIRED wrote up an article about it here: https://www.wired.com/story/mcdonalds-ai-hiring-chat-bot-paradoxai It's an interesting story, that leans heavily on fears about AI being unreliable and unsecure etc. I'm sure it got plenty of clicks, but Andy Greenberg missed the point.
Yes, McDonald's has a piece of shit recruitment chatbot. Or, more accurately, they paid Paradox to integrate their shitty AI chatbot into the maccas ERP and slap the golden arches logo on it. But, the cybersecurity issues are not caused by AI. That's just clickbait smeared on top.
Do you have any idea just how many things have to go wrong for this cybersecurity incident to have occurred? The amount of incompetent asshats that need to be involved (or not involved, as it were)?
What we have here, kids, is called Systemic Failure.
I love the term. It just rolls off the tongue, like “12 month consulting and remediation project, 5 people, billed T&M plus expenses”.
Systemic Failure is when your corporation fucks up, then does it again and again and again, and no matter how hard you try, it just seems to keep happening. By all appearances, Paradox (and McDonald's) have systemic failures in their cybersecurity implementation and governance.
Here's the real story about McDonald's chatbot failure
Maccas needed an app to streamline recruitment. Trawling through their target market of child labour and people desperately needing income is a lot of, well, work. It's expensive and slow. So someone decided to automate the hell out of it and use an LLM (AI) as the happy interface to replace HR.
So far, so good. It's not a terrible idea, to be honest.
An exec would have asked “how hard can it be?” and gotten an answer with lots of zeros in it. Too many zeros, and too many months. So after a quick google, they came up with a new plan: “Paradox.ai says they can do it for a fraction of that and in just x months!”.
Paradox's tagline is literally:
“Conversational recruiting software that automates the work your teams don't have time for.”
It's a match made in heaven.
And right there is where it went to shit for McDonald's. Not the test user account that wasn't disabled back in 2019, and not the AI integration. The real story, is a sadly common one in the cybersecurity industry:
- These companies failed at their basic cybersecurity obligations
- As usual, nobody important will get held accountable
Let's break this down a bit, so it's easy to see the failure.
Who/what is Paradox anyway?
A tech company started back in 2016 that provides a conversational AI agent for recruitment.
Their real value-add is not the chatbot “Olivia” though, it's the back end integrations. They have done the grunt work of hooking it into all the major ERP services like Workday, HCM and SAP. Nobody wants to run a project with custom SAP integration, that shits a nightmare. Far easier to pay a SaaS provider for a working solution.
- Paradox has raised a fucktonne of cash ($250M+ USD) and is valued at over $1.5B USD.
- They have about 800 staff, with the bulk of the developers in Vietnam.
- On their website, Paradox say they are PCI 27001 and SOC 2 Type II compliant: https://www.paradox.ai/legal/security
So how can a $214B company hire $1.5B company, who then exposes the details of 64 million people?
According to Paradox, it's simple: Someone forgot to reset a password. Hahahahaha silly engineers. But don't stress, it's all fixed now 🤣🤞
Official version here: https://www.paradox.ai/blog/responsible-security-update
Critical Observations
Let's look at the things Paradox had to fuck up to create this password issue. To add some validity to my ranting, let's look at it through the lens of ISO 27001 standards. After all, both Paradox and McDonald's hold this certification so they should be familiar with the framework.
We'll need:
- Identify core issues
- My industry insights (rant)
- ISO27001 relevant guidance
Identity & Access Management Failures
Orphaned Test Accounts
- The test admin account (“123456”) had not been used since 2019. This implies no account lifecycle management, no account review policies, and poor governance.
- ISO27001:A.9.2 to 9.4 Removal or adjustment of access rights
Test Account Accessing Production Data
- Indicates no environment separation. Test/staging accounts should never have access to production databases.
- ISO27001:A.9.1.2 Access to networks and network services
Lack of RBAC (Role-Based Access Control)
- The test account had broad access to data that should have been scoped. There was no enforcement of least-privilege principles.
- ISO27001:A.9.1.1 Access control policy
No SSO or Identity Federation
- The use of standalone credentials suggests no integration with an identity provider (IdP) or corporate directory, which would have allowed central account control, auditing, and provisioning.
- ISO27001:A.9.2.2 User access provisioning
No Multi-Factor Authentication (MFA)
- Logging in with a weak password and no MFA indicates a total absence of baseline identity security controls.
- Yes, it could theoretically be an account used for systems testing, but it's also used by humans. So fucking use MFA.
- ISO27001:A.9.4.2 Secure log-on procedures
Application & Data Architecture Failures
IDOR (Insecure Direct Object Reference) Vulnerability
- Researchers could increment/decrement application IDs to access other users' data. This is a textbook example of broken access control.
- This is really, REALLY, basic stuff. Orgs this large shouldn't have these kinds of graduate level errors
- ISO27001:A.14.2.8 System security
Over-permissive Data Access
- The chatbot could access all applicant data, including names, emails, and phone numbers, despite not needing that data to operate. This violates the principle of least privilege.
- ISO27001:A.10.1.1 Policy on the use of cryptographic controls
No API Gateway or Middleware Access Control
- There's no indication that access was validated at multiple layers (e.g., token scopes, query constraints, or tenancy isolation at the API/data layer).
- Where was the AWS WAF?
- ISO27001:A.9.4.1 - Information access restriction
No Logging or Monitoring for Abnormal Access
- No intrusion detection or anomaly monitoring caught the sudden access to 60+ million records using an outdated account. There should have been SIEM or alerting tools watching for unusual data queries.
- Let me guess, you've got one, but nobody ever checks the events or is auto-binning the emails?
- ISO27001:A.12.4.1 Event logging
DevOps & Deployment Process Weaknesses
Lack of CICD Hygiene
- The fact that test accounts and test infrastructure persisted since 2019 suggests CICD pipelines do not include post-deployment cleanup of temporary users/resources.
- If this account is used for automated testing such as integration / end-to-end testing, then it shouldn't even need a known password.
- Where is the change control if this is a testing account for humans?
- ISO27001:A.14.2.2 System change control procedures
Shared accounts
- Why are multiple people sharing a single testing identity?
- Why is the test identity generic and easily missed?
- ISO27001: A.9.2.1: User registration and de-registration
No Infrastructure-as-Code Enforcement
- Environments were clearly not reproducible or ephemeral. With IaC, old/deprecated resources like this account would be versioned out or destroyed regularly.
- Non production environments should be regularly purged with cleansing fire. There is no excuse to have old accounts lying around.
- ISO27001:A.14.2.1 Secure development policy
Production Data Was Not Tokenised or Redacted in Test Contexts
- Allowing production data to be read or even exist in a test-linked account demonstrates a lack of data sanitisation or segmentation.
- You just know the prod data has spread through these systems like herpes. I'd bet a year's worth of OpenAI tokens that the sales team has it exported to Excel on their laptops.
- ISO27001:A.14.3.1 - Protection of test data
Security Practices & Organisational Maturity
- No Penetration Testing or Secure Code Review
- Basic vulnerabilities like weak passwords, IDORs, and access controls should have been found in internal security assessments or by an external audit.
- ISO27001:A.14.2.8 System security testing
No Bug Bounty Program Until After the Breach
- The article mentions the launch of a bug bounty after being notified of the breach, indicating reactive rather than proactive security culture.
- A bug bounty is also a piss poor way to deal with internal security governance issues.
- ISO27001:A.16.1.2 Reporting information security events
No Public Security Disclosure or Transparency Report
- Confirmation and handling came only after media outreach. There's no indication of a responsible disclosure program or notification process for affected users.
- ISO27001:A.16.1.4 Assessment of and decision on information security events
That's a good starting point.
So, is security a real focus at Paradox?
When you see a company delivering systems this poorly, you've got to wonder how seriously they take cybersecurity. Obviously, vendors will make plenty of promises, but what evidence (or lack of) do we have that they make a real commitment to securing their systems?
>Staff<
Check the headcount. Cybersecurity is complex and expensive, even more so in a rapidly scaling and changing tech company. If they are doing it, you'll see it in the headcount.
If I look up Paradox on LinkedIn, I see 815 associated members. Let's call it 800 on the safe side.
- They have a CIO, but he is on the board and not dealing with technical issues
- I can't find any records of them having a CISO or CTO
- There are only 24 staff with “security” in their profile
- Of those 24, only 3, have experience as full-time cybersecurity professionals
3 staff, out of 800, to provide cybersecurity for a $1.5B company that holds 10s (if not 100s) of millions of PII records.
Those 3 people are doing an awful lot of heavy lifting to meet Paradox's claim of:
"Paradox is committed to your data security and privacy”
No tech/security function even made the leadership page. An interesting take on leadership, for an AI-driven tech company. https://www.paradox.ai/about/leadership
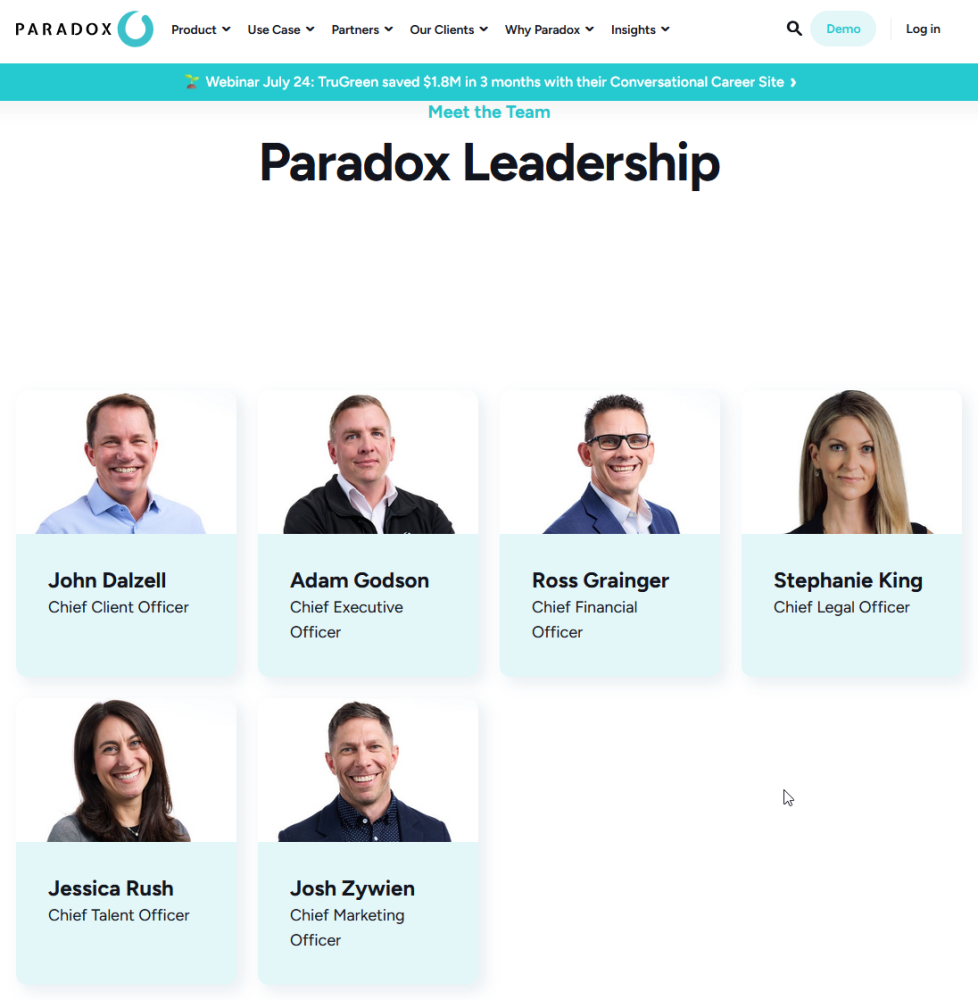
Hello? Is the CISCO there? Olivia?
McDonald's can't sidestep this failure, btw
ISO 27001 requires supplier security agreements (A.15.1.1) and periodic audits or reviews of third parties (A.15.2.1).
McDonald's failed to ensure Paradox met baseline controls. I'm sure they asked. Probably sent them a comprehensive spreadsheet of items to tick off before the commercials were signed. But nobody checked.
This breach applied to the global recruiting activities of McDonald's. While they attest no data was taken by other parties, any breach would trigger privacy regulations in the EU, UK, and Australia. Moreover, many of those applicants were minors, so aspects of the GDPR, UK ICO and Australian Privacy Act.
Now, McDonald's does have a CISO. Looks like they actually have several Mike Gordon, Nate Partridge and Jerome Pickett M.B.A., M.A. (Maybe loan one to Paradox?). I'm sure one of them signed off on the Paradox contracts and governance 🤔
But hey, it's just a password, right?
Yes and No.
Sure, they dodged a bullet and some friendlies found the issue before a ransomware crew did. It looks like no data was stolen and they have removed the vulnerable account. Many would say it's not that big a deal at this point. Maccas sure as fuck is.
Except its systemic failure, remember? When a company fucks up like this, you just know it's part of the culture and operating model. Especially a startup. That VC money was meant to 10x the $250M, not piss around with delays due to security and governance. They want to go fast and scoop up market share before the cash runs out.
Which means they make a mess and don't spend budget on cleaning up as they go. That “Tech debt” just stacks up, to be dealt with post IPO.
So you end up with things like old accounts, bad password and shitty Route53 subdomains for mchire.com
- api-k8s.mchire.com
- Dead, but thanks for letting me know you use Kubes
- api-k8s.stg.mchire.com
- same
- chrome.mchire.com
- Why do you have a dead NGINX box on the net?
- Do you not have systems monitoring?

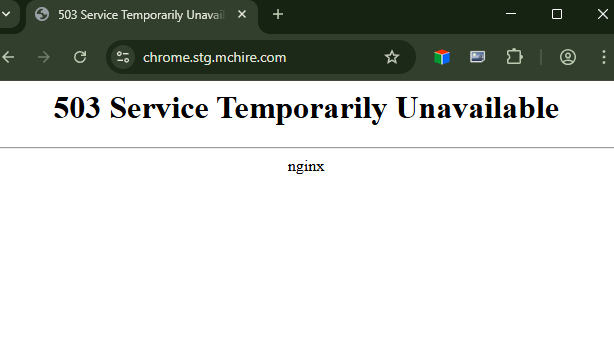
- chrome.stg.mchire.com
- Another NGINX
- chromecf.mchire.com
- Misconfigured/empty CloudFront instance

- chromecf.mcstg.mchire.com
- Another misconfigured CloudFront
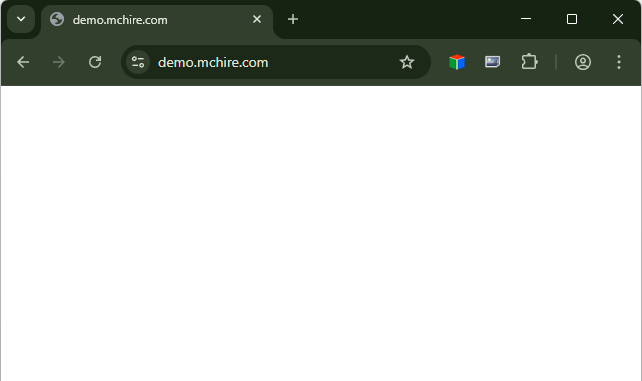
- demo.mchire.com
- Heads up, your demo doesn't load
- oh, and don't use *. TLS certs. Certificate Manager certs are basically free.

- demo.www.proxy.mchire.com
- dead
- genai.mchire.com
- If this is an API, you should always demand auth, not give me a 404

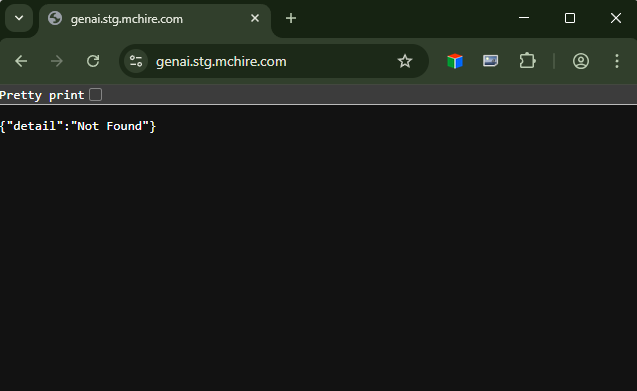
- genai.stg.mchire.com
- Aim to keep your non-prod off the internet
- VPN is cheap these days
- jobs.mchire.com
- That's unfortunate...
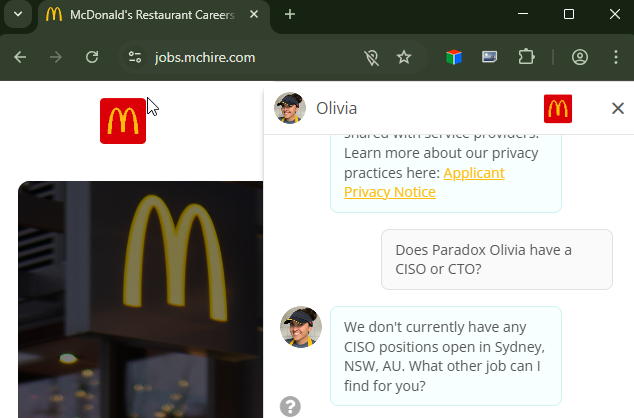
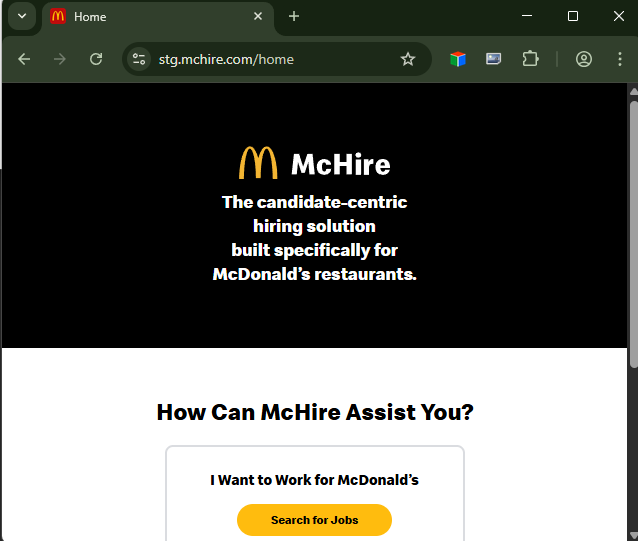
- stg.mchire.com
- Pro tip. Staging should always be one deploy behind prod, not a test deploy
- stgapi.mchire.com
- Hey! You got this one right with a 403, go team!

- stgchrome.mchire.com
- You guys really struggle with NGINX hey?
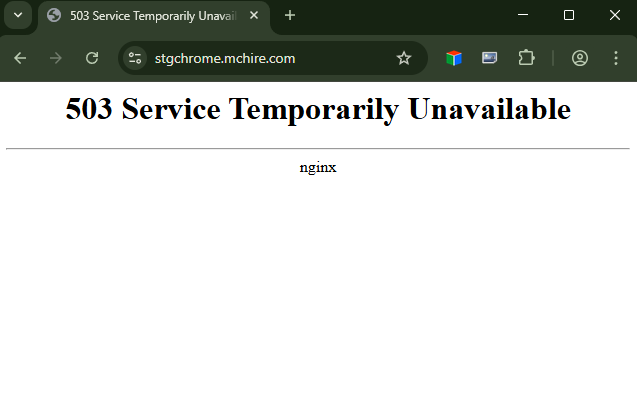
So yeah...
AI gets a lot of shit recently, but humans are still better at building crap cybersecurity.
THE END